The world of IoT is expanding rapidly, bringing with it a growing demand for scalable, secure, and efficient device management solutions. Traditional approaches often struggle with the complexities of managing heterogeneous fleets of devices while ensuring secure operations and reliable software delivery. Our Cloud-Native IoT project addresses these challenges by leveraging k8s to provide a unified, highly automated, and secure ecosystem tailored for IoT environments.
At the core of this architecture is Akri, which acts
as the critical bridge between k8s and the diverse array of IoT devices in a
fleet. Akri enables seamless discovery and management of IoT devices,
treating them as integral components of the k8s ecosystem. This integration
eliminates many of the manual steps traditionally required in IoT deployments,
allowing developers to deploy and manage applications across devices with the
same ease as managing containerized workloads in the cloud.
Understanding Akri’s Architecture
Link to heading

Akri’s architecture is designed to extend k8s’ capabilities to IoT devices,
creating a unified interface for managing workloads across cloud, edge, and IoT
layers. It achieves this through three core components: Akri Controllers, Akri
Brokers, and k8s Custom Resources.
The Akri Controller operates within the k8s control plane, continuously
monitoring for available IoT devices by interacting with various device
plugins. These plugins are responsible for identifying devices such as cameras,
sensors, or other hardware endpoints, which might be connected via USB, network
protocols, or proprietary interfaces. When a device is detected, the Akri
Controller registers it as a k8s resource by creating a corresponding custom
resource (CR). These CRs make IoT devices discoverable and manageable using
k8s-native tools, enabling seamless integration with containerized workloads.
Figure 1: 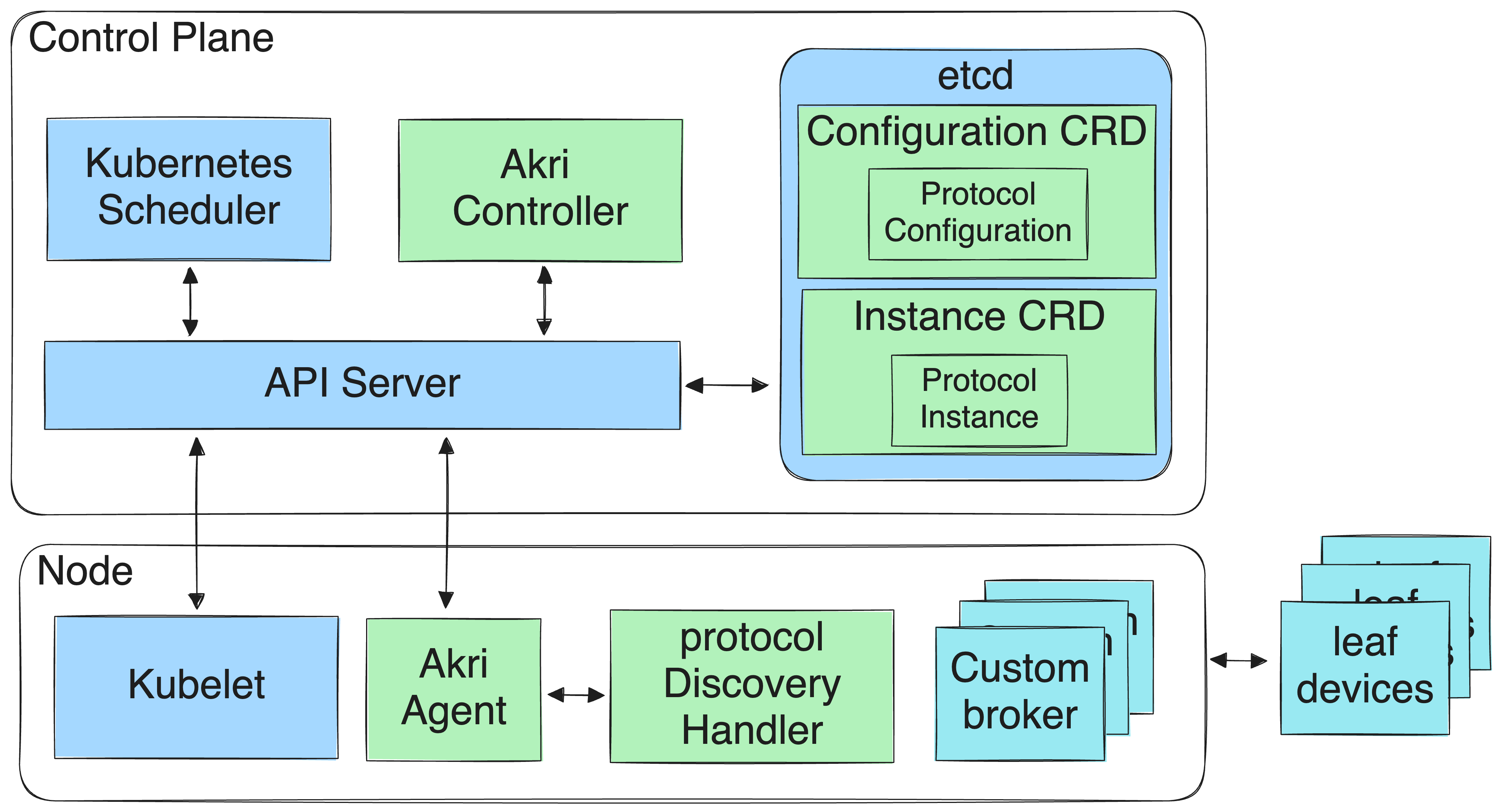
Akri’s ArchitectureAkri Brokers come into play. Brokers are
lightweight, containerized components deployed as k8s pods to manage the
interaction between k8s workloads and the IoT devices they rely on. For
instance, if an application requires access to a specific camera or sensor, the
Akri Broker ensures the application receives the appropriate connection and
data from the device. Multiple brokers can run simultaneously, each tailored to
specific device types, ensuring scalability and flexibility across diverse
environments.
Akri’s architecture enables dynamic device discovery and usage. Whether a
device is added or removed, Akri automatically updates the cluster’s state,
reflecting the current device inventory. This dynamic nature makes it
particularly well-suited for environments where IoT devices may frequently
change, such as smart factories or mobile deployments. By abstracting the
complexities of device management, Akri allows developers to focus on building
and deploying IoT applications rather than wrestling with the nuances of device
connectivity. For more information on our engagement with Akri please have a
look at our previous experiments.
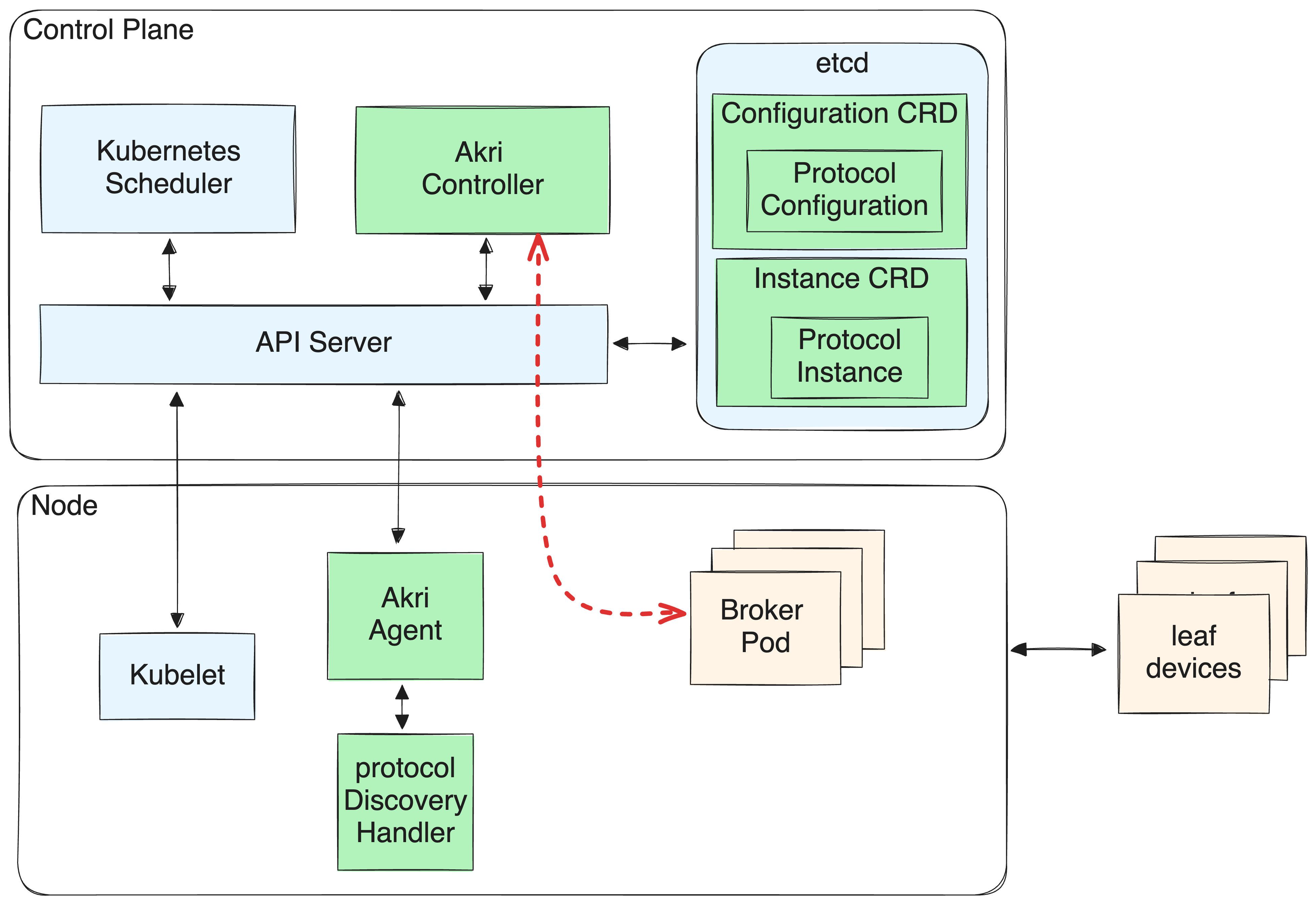
Figure 2: Akri’s steady state IoT device handling
Beyond Application Management: Secure & Efficient OTA Updates
Link to heading
While Akri provides a robust foundation for integrating IoT devices with k8s,
our architecture goes further to address critical challenges like simplified
software delivery, trusted execution and secure on-boarding.
FlashJob Operator & CRD
Link to heading
First, we build a simplified operator and CRD to handle application deployment
on IoT devices. We follow the same principles as Akri (and our previous
attempts), but we decouple the firmware flashing operation from the inventory
setup and discovery of devices: essentially, we let Akri do the heavy lifting
of populating the k8s-related structures with device info, and use this
information to initiate a firmware flash operation.
The operator subscribes to Akri instances (the device entries in the k8s
database) and, when needed, is able to retrieve information about each device.
For instance, the operator is able to query the database for the device unique
ID, its network endpoint, firmware version, application type etc.
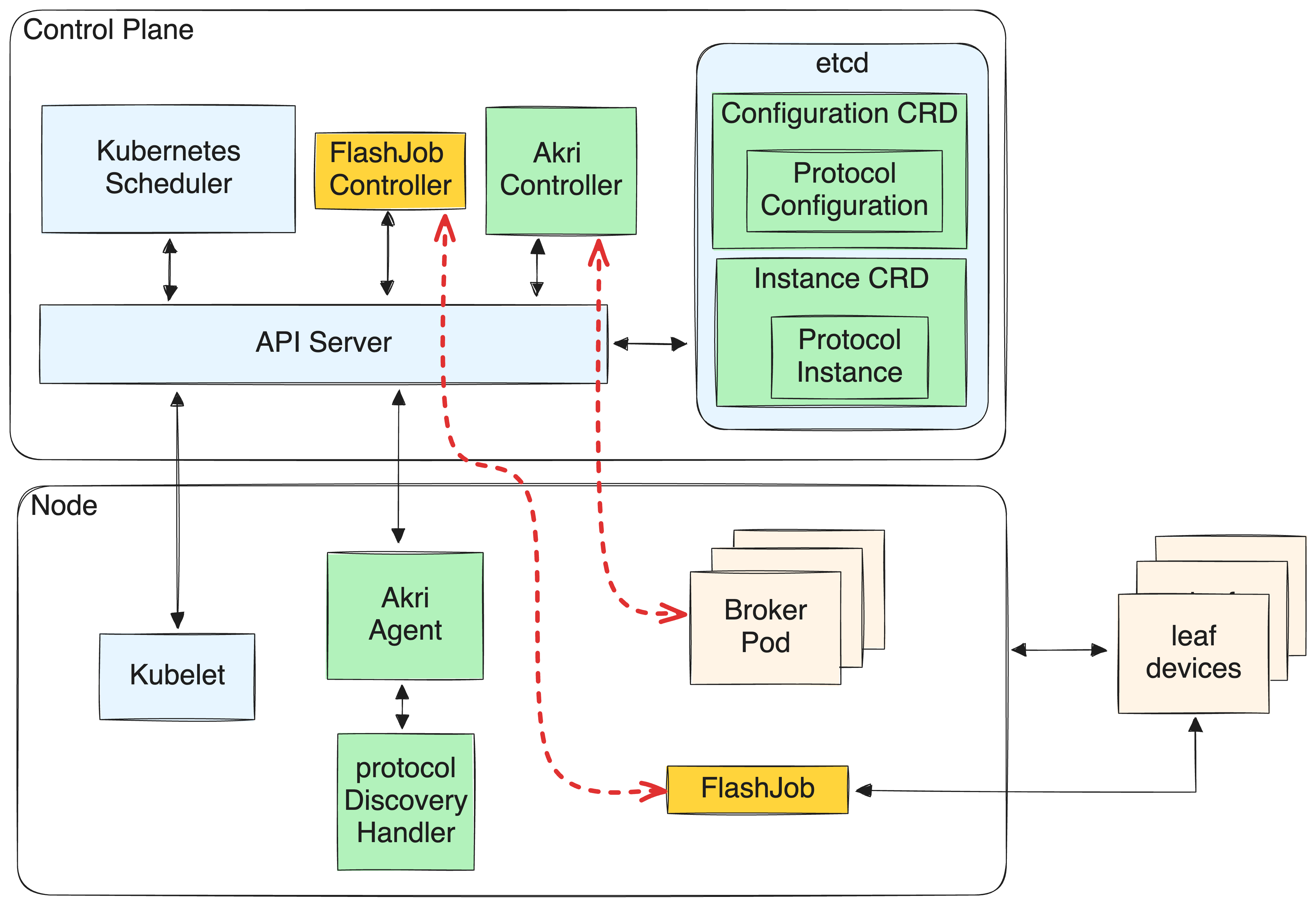
Figure 3: FlashJob spawn and IoT device update
When a request reaches the operator for a firmware flash on a set of devices,
the operator fetches the relevant information from the database and spawns a
FlashJob Pod with this information that initiates the OTA mechanism for the
specific devices. The IoT devices are updated, and, in turn, re-discovered by
the relevant discovery handler of Akri. For instance, if the update refers to
device re-purposing (running a different application than previously), the
relevant discovery handler will detect new devices, whereas the former
discovery handler will update that the old device is not reachable, and it will
be removed from the specific inventory entry.
To facilitate software delivery, the FlashJob Pod fetches the firmware blob
that will be flashed onto the device from a container registry.
OCI firmware packaging Link to heading
Firmware blobs are packaged as OCI artifacts, which can be stored in any
OCI-compliant registry. These artifacts are designed to support multiple
devices and configurations, minimizing the burden of managing diverse hardware
across a fleet. The FlashJob operator that orchestrates updates, fetches only
the relevant parts of the artifact for each device, reducing bandwidth usage
and streamlining the delivery process.
To further optimize the workflow, we build a simple
pipeline that, given the source code
of an application ported to an IoT device framework (such as ESP32-based
devices, with esp-idf), builds the binary blob, packages it as an OCI image
and creates an image manifest, annotating each OCI image with the relevant
architecture/platform. These images and manifests are pushed to a generic
container registry.
On the FlashJob side, we use generic tooling and mechanisms to fetch the
relevant firmware blob that matches the device to be updated.
Zero-touch and Zero-trust security considerations Link to heading
Integrating a secure device on-boarding and over-the-air (OTA) update
framework, ensures that only authenticated devices join the cluster, and that
software updates are delivered optimally, with minimum overhead, without
compromising security.
The secure on-boarding and OTA update framework is built on
OpenDICE, a lightweight
attestation and identity management solution. This framework leverages
device-specific secrets to derive cryptographic keys, which are used to
generate unique device certificates. These certificates play a pivotal role in
signing EAT (Entity Attestation
Tokens), embedding
critical device metadata such as the application type, firmware version, and
other relevant attributes.
Devices send these signed EATs to key system components, such as the discovery handler, enabling robust device attestation. This process verifies device authenticity and enforces strict access control policies, ensuring that only authorized devices can communicate and interact within the system.
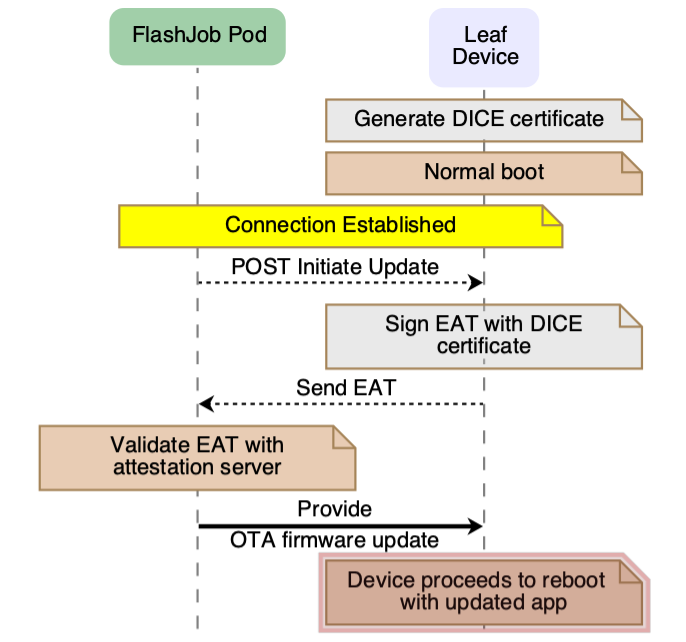
Figure 4: IoT device OTA update workflow
For OTA updates, the framework issues updates exclusively to trusted platform
components, maintaining integrity and security throughout the update process.
When paired with a secure boot mechanism, the framework ensures that devices
start in a trusted state immediately upon powering on. Together, these features
establish a strong foundation for trust, security, and reliability across the
entire lifecycle of the device—from initialization to operational updates.
Use Cases Link to heading
Our Cloud-Native IoT framework has applications in a wide range of industries, each with unique requirements that benefit from the architecture’s flexibility, security, and scalability.
In manufacturing, smart factories can leverage this architecture to manage
fleets of sensors, robotic arms, and edge devices. With Akri’s dynamic device
discovery and k8s’ orchestration capabilities, factories can deploy multi-tier
applications that span cloud-based analytics, edge-based processing, and
IoT-based data collection. Secure on-boarding and trusted OTA updates ensure
that only authorized devices operate in these environments, minimizing risks
associated with counterfeit hardware or outdated firmware.
In healthcare, where compliance and data integrity are critical, our framework
enables secure deployment and management of medical IoT devices, such as
patient monitors or diagnostic equipment. By packaging software updates as OCI
artifacts, healthcare providers can ensure consistency across devices while
adhering to strict regulatory standards. Akri’s ability to dynamically discover
and manage devices also simplifies the deployment of new technologies in
hospital settings.
The retail industry can benefit from deploying smart shelves, cameras, and
IoT-enabled inventory systems using this architecture. The ability to deliver
targeted OTA updates based on device-specific requirements ensures that
software upgrades don’t disrupt operations, even during peak business hours.
Additionally, secure on-boarding mechanisms guarantee that only authorized
devices interact with sensitive business systems.
In addition to traditional IoT applications, device re-purposing opens new
opportunities for innovation by enabling the same hardware to perform entirely
different functions depending on operational needs. For example, devices
running tinyML applications, can be dynamically re-purposed to execute a
different model, or even application, bringing flexible and adaptable machine
learning inference at the edge.
In the case of a smart camera in a retail environment, deployed for security
purposes – the same device can be repurposed to run a tinyML-powered model for
customer analytics, such as tracking foot traffic or identifying
high-engagement areas within a store.
In agriculture, an IoT sensor initially configured to monitor soil moisture
could be repurposed to run a tinyML model detecting crop diseases based on
image data captured by an attached camera.
Similarly, in industrial settings, robotic arms used for assembly line tasks
can be reprogrammed to perform quality assurance using tinyML models for
anomaly detection.
This flexibility eliminates downtime and minimizes costs associated with
dedicated hardware for each task. Re-purposing is not only secure and
efficient, but also highly adaptable, enabling a single fleet of devices to
cater to multiple use cases across industries. Users can easily transition
devices to support various tinyML workloads or other specialized applications
as required.
Conclusion Link to heading
By combining k8s with IoT-specific innovations, our Cloud-Native IoT project
provides a scalable, secure, and efficient solution for managing IoT devices.
Akri’s architecture brings dynamic device discovery and integration into the
k8s ecosystem, while the secure on-boarding and OTA update framework ensures
that devices operate reliably and securely throughout their lifecycle. The
OCI-compliant process of packaging the firmware blob facilitates the
cloud-native integration of IoT device re-purposing.
This approach empowers end-users to deploy complex applications across cloud, edge, and IoT layers with ease, opening up new possibilities for automation, intelligence, and operational efficiency. As IoT continues to reshape industries, adopting a cloud-native framework will be essential for staying ahead in this rapidly evolving space.
Stay tuned as we push the boundaries of what’s possible with Cloud-native IoT!